I - Prologue
It has been nearly 6 years since the infamous ransomware crisis known as 'Wannacry' affected most countries around the world. However, to this day, this malware is still frequently mentioned in discussions within the field of information security and has also served as inspiration for subsequent ransomware strains.
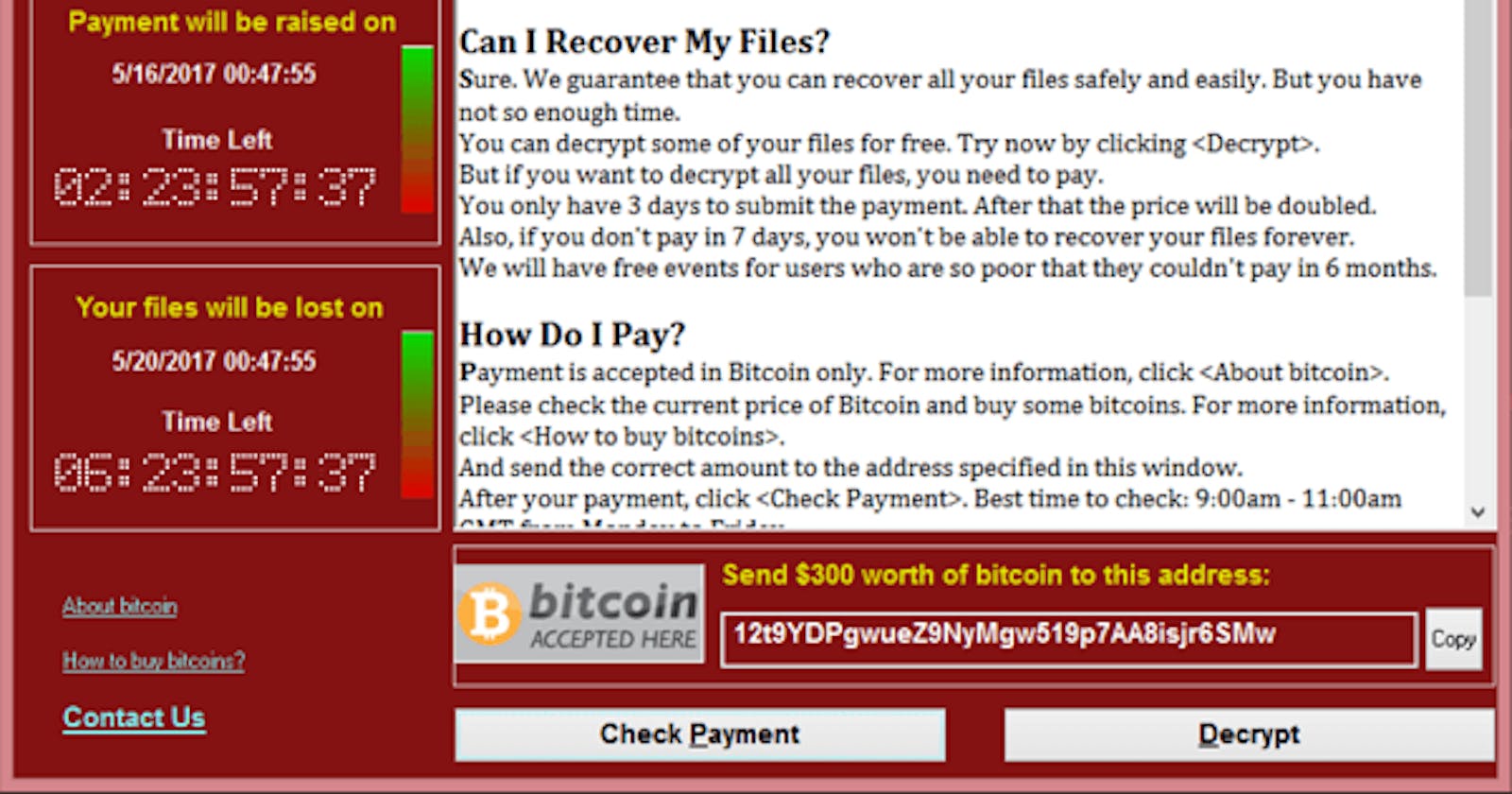
To help people understand more about Wannacry and ransomware in general, today BlueCyber will provide you with a detailed analysis of the WannaCry ransomware sample that was active in the years 2017 and 2018.
The Malware sample we used has a hash of 84c82835a5d21bbcf75a61706d8ab549
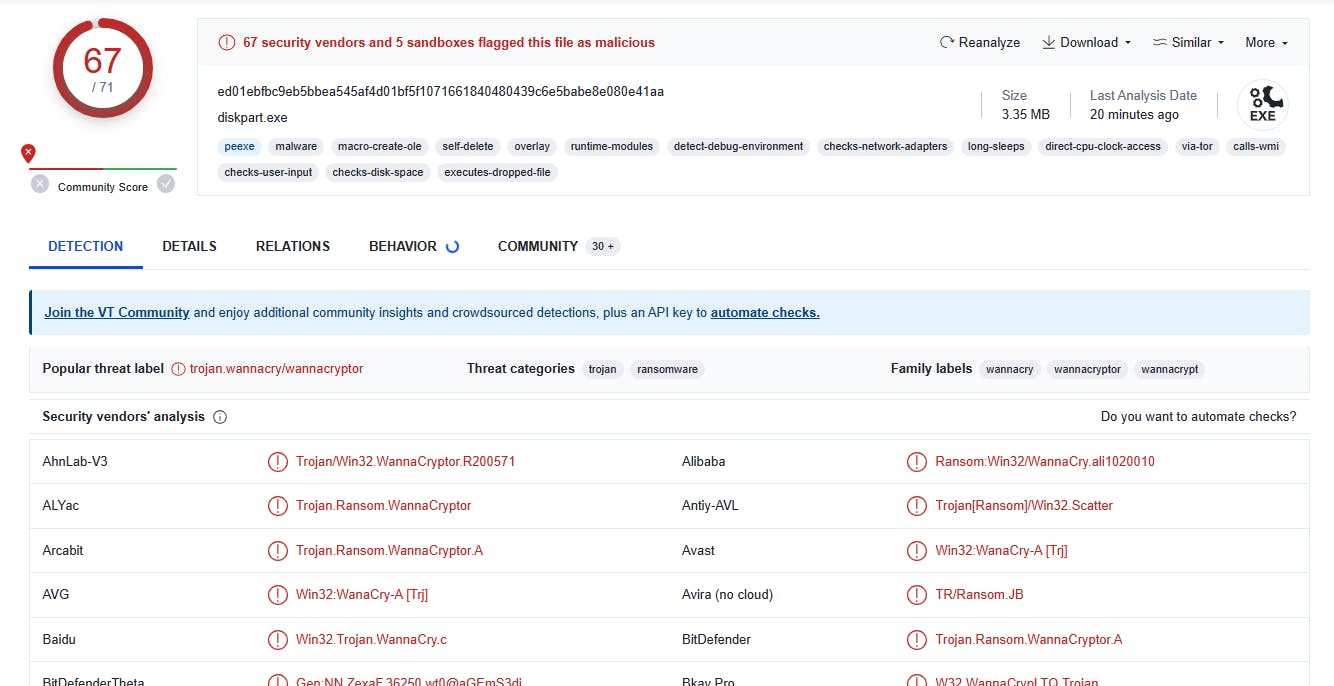
II - Overview
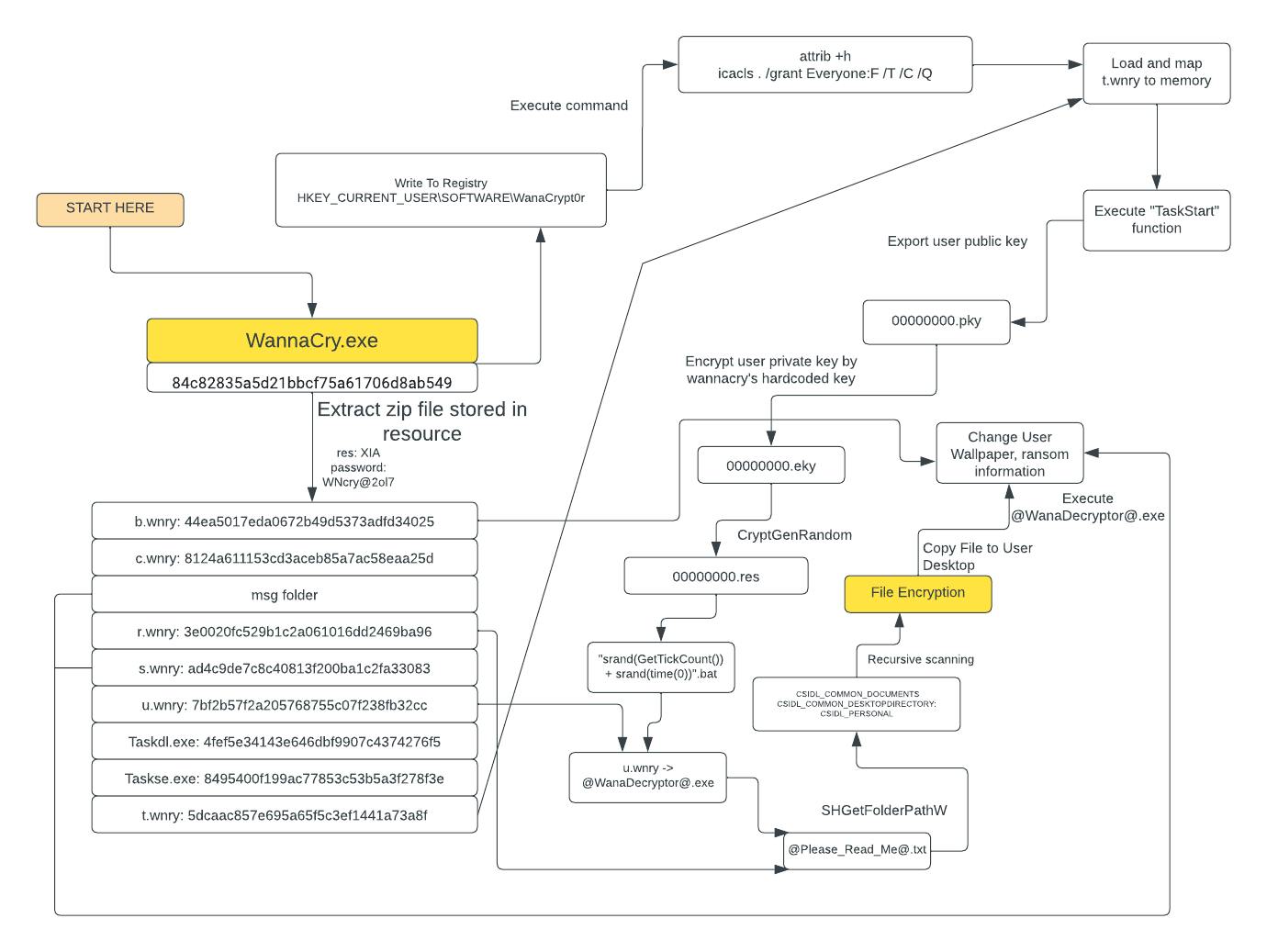
This is the malware's working flow
III - In-Depth Analysis
1. Write to Registry
First, the malware creates and writes the key HKCU/Software/wd (or HKLM/Software/wd if it has high privileges). The value of the key is set to "wd," which represents the current directory of the malware when it is executed.
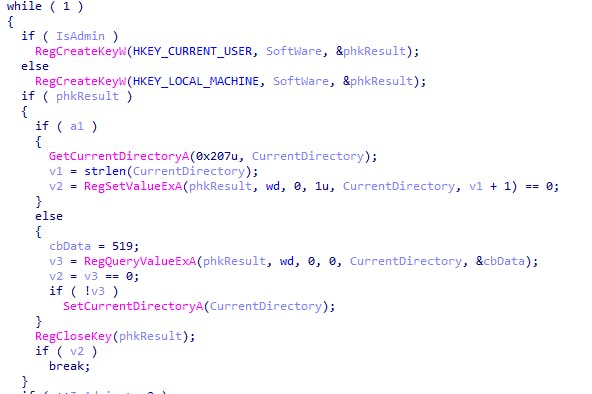
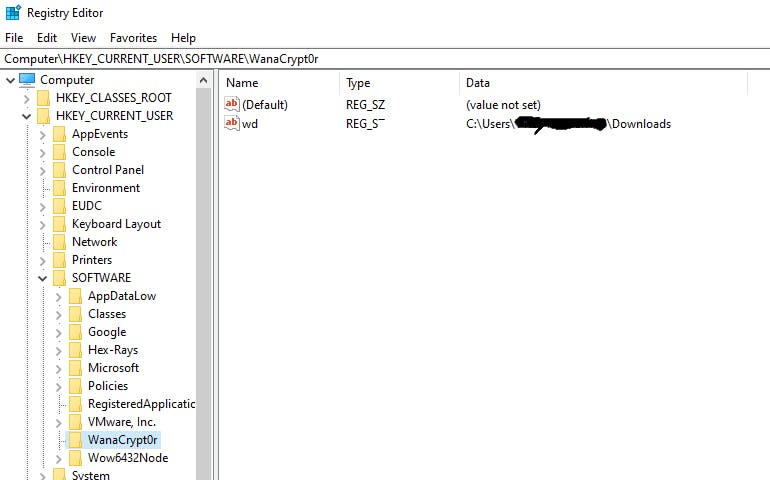
By doing this, the malware can check whether it has already been executed on the system or not, as well as remove itself afterwards.
2. Extract resource
WannaCry stores a binary named "XIA" within its own Resource section. This Resource is a password-protected zip file that is compressed. The malware then extracts the Resource using a password "WNcry@2ol7" that is hardcoded in the malicious code.
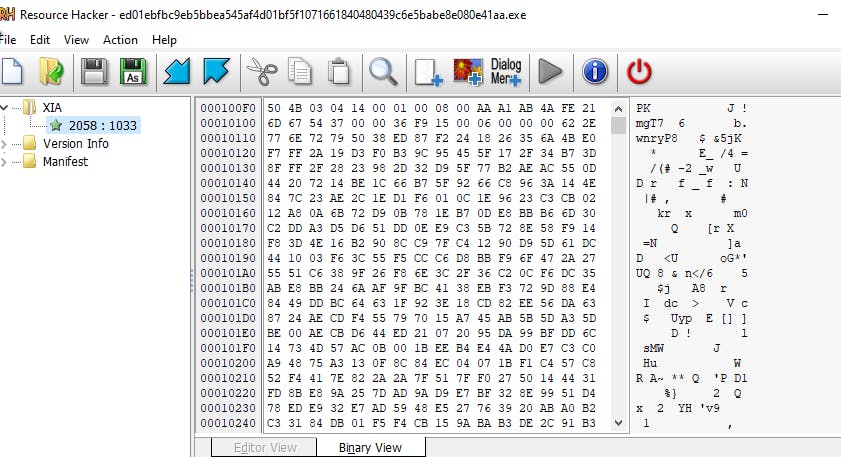
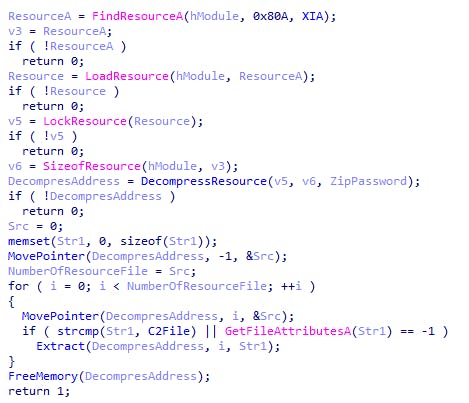
The list of files extracted from the resource includes:
b.wnry: A bitmap file renamed as the background image.
c.wnry: A list of C2 (command and control) servers and links related to the TOR browser.
Folder msg: Contains RTF files that serve as notifications to the victims about the encrypted files in various languages.
r.wnry: Contains Q/A (question and answer) files.
s.wnry: A zip file containing the TOR browser installation program.
t.wnry: Contains encrypted DLL files, which are decrypted and loaded into the current process to carry out file encryption.
u.wnry: The interface program of the malware that prompts the user to make ransom payments and changes the victim's background image.
Additionally, there are two .exe files:
taskdl.exe
taskse.exe
3. Set file attributes
The malware executes two commands to change the attributes of files in the current folder, including:
Set all files in the current folder to the hidden attribute using the command '
attrib +h'.Grant Full Control permission to Everyone on all files in the current folder using the command:
icacls . /grant Everyone:F /T /C /Q.
Here are the explanations of the parameters:
/grant: Grants permissions.Everyone:F: Grants Full Control permission to all users./T: Applies to all subfolders within the current directory./C: Continues the operation even if errors occur./Q: Suppresses the display of success messages.
4. Decrypt DLL and map it into the process
The malware decrypts the file t.wnry (file encrypted by the malware's own algorithm). After decryption, the file t.wnry becomes a DLL file that contains encryption algorithms.
The malware proceeds to map the code of the DLL into its own memory and executes the function named "TaskStart" within that DLL.
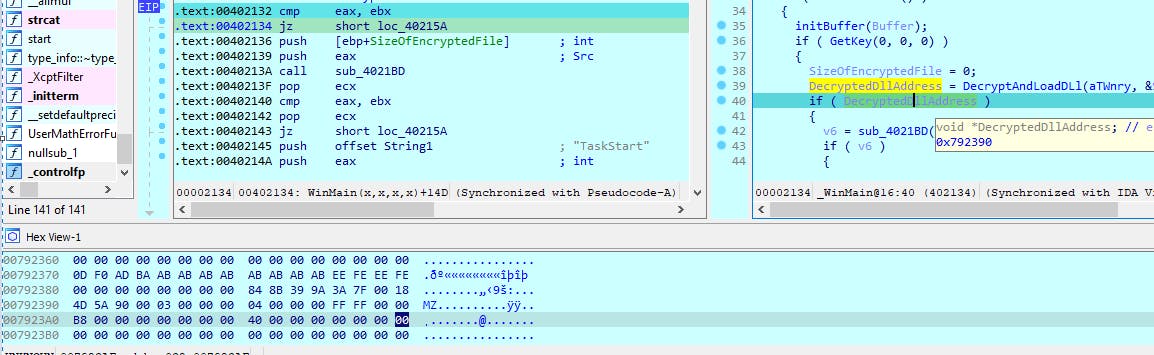
You can use this simple IDC script to dump that dll out
imort idc
begin = 0x792390
Size = 0x10000
DllData = idc.get_bytes(begin, Size, 0)
DllFile = open("dump.dll", "wb")
DllFile.write(DllData)
DllFile.close()
print("Done")
The dumped file has hash: f351e1fcca0c4ea05fc44d15a17f8b36
The malware maps the DLL into its own process and executes the "TaskStart" function.
This DLL file serves the purpose of searching for and encrypting files on the victim's machine.
5. Import, Export and Encrypt user keys
The malware exports the User's public key to a file named 00000000.pky using the CryptExportKey function.
The User's private key is encrypted using a Key hardcoded in the program.
The CryptDestroyKey function is used to immediately delete the private key after the encryption process.
8 random bytes generated from CryptGenRandom are written to the file 00000000.res
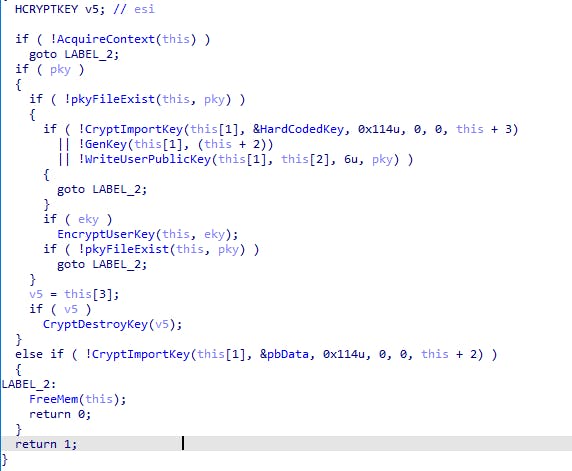
In the following part, we will provide a detailed explanation of the encryption algorithm used in the malware and how the malware searches for files on the victim's machine!